In today’s interconnected digital landscape, the ability to open and manage specific ports on a server is a skill that can significantly impact your server’s performance, security, and functionality. Whether you’re a seasoned system administrator, a web developer, or someone who simply wants to gain a deeper understanding of server management, this comprehensive guide will equip you with the knowledge and techniques needed to navigate the world of server ports effectively.
Understanding Server Ports
Before we dive into the intricacies of opening specific ports, let’s establish a clear understanding of what server ports are and why they matter. In the context of networking, a port is like a virtual doorway that allows data to enter or exit a server. Each port is associated with a unique number, ranging from 1 to 65535, and is used to identify different services and applications running on the server.
Why Open a Specific Port?
The process of opening a specific port is crucial for various reasons:
- Service Accessibility: Opening ports enables specific services or applications to communicate with the server. For example, port 80 is commonly used for HTTP web traffic, while port 22 is reserved for SSH access;
- Firewall Configuration: Ports are a fundamental aspect of firewall configuration. By opening or closing ports, you can control which incoming and outgoing traffic is allowed or blocked;
- Enhanced Security: Properly configuring and managing ports can enhance server security by limiting access to only authorized users or systems.
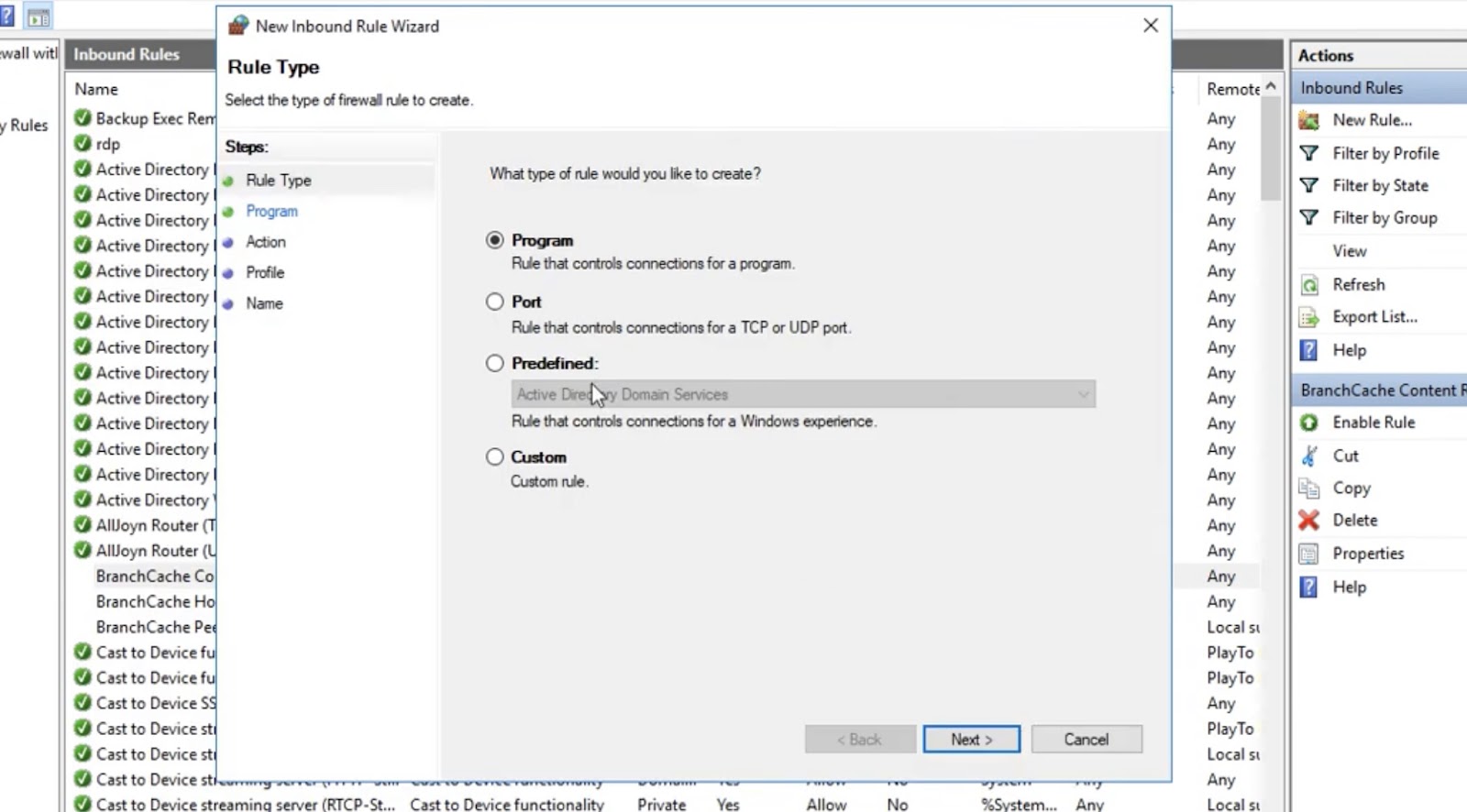
Step-by-Step Guide to Opening a Specific Port
- Identify the Port: The first step is to determine which port you want to open. Consider the specific service or application that requires access to this port;
- Access Server Settings: Depending on your server’s operating system, access the server settings. On a Linux-based server, you might use SSH, while on a Windows server, you’d typically use Remote Desktop Protocol (RDP);
- Edit Firewall Rules: Use firewall management tools, such as iptables for Linux or Windows Firewall for Windows, to add a rule that allows traffic on the chosen port;
- Test Connectivity: After configuring the firewall rule, test the connectivity to ensure that the port is open and functioning correctly;
- Monitor and Maintain: Regularly monitor your server’s ports to ensure they remain secure and properly configured. Update firewall rules as needed.
Advanced Port Management
For those seeking a deeper understanding of port management, consider exploring topics such as:
- Port Forwarding: Redirecting incoming traffic from one port to another;
- Security Considerations: Best practices for securing open ports, including the use of intrusion detection systems (IDS) and intrusion prevention systems (IPS);
- Load Balancing: Distributing incoming traffic across multiple servers using load balancers.
Port Management Techniques
- Port Forwarding:
Port forwarding is a powerful technique that allows you to redirect incoming traffic from one port to another. It’s particularly useful when you want to expose a service running on a non-standard port to the outside world.
To set up port forwarding, access your router’s settings and create a rule that maps an external port to an internal port on your server.
Use cases for port forwarding include hosting a web server (HTTP on port 80) behind a router or enabling remote access to a specific service.
- Dynamic Port Allocation:
Some applications use dynamic port allocation, which means they select an available port at runtime rather than using a predefined port.
While this can make network configurations more flexible, it can also pose challenges for firewall configurations and security. You may need to allow a range of ports for such applications.
Security Considerations
1. Intrusion Detection and Prevention:
Opening ports, especially to the public internet, can expose your server to potential security threats. Implement intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor and respond to suspicious activity.
IDS tools like Snort or Suricata can alert you to potential security breaches, while IPS can actively block malicious traffic.
2. Two-Factor Authentication (2FA):
If you’re opening ports to allow remote access to your server, consider implementing two-factor authentication for an added layer of security.
2FA requires users to provide two authentication factors (usually something they know, like a password, and something they have, like a smartphone) before gaining access.
3. Regular Audits:
- Periodically audit your server’s open ports to ensure they are still necessary. Close any ports that are no longer in use to reduce the attack surface;
- Automated scanning tools like Nmap can help you identify open ports on your server.
Load Balancing
1. Load Balancers:
- Load balancers distribute incoming network traffic across multiple servers to ensure optimal resource utilization, high availability, and fault tolerance;
- Popular load balancing solutions include HAProxy, Nginx, and cloud-based services like AWS Elastic Load Balancing.
2. Port Load Balancing:
- In addition to distributing traffic across multiple servers, load balancers can also perform port-based load balancing;
- This means that they can distribute traffic based on the port number used in incoming requests, allowing you to balance different services across your server farm.
Scalability and High Availability
1. Scalability:
- When your server’s traffic load increases, you may need to scale your infrastructure to handle the demand. Scalability is the ability to expand your resources seamlessly to accommodate higher workloads;
- One common approach to scaling is horizontal scaling, where you add more servers to your infrastructure. This can be done manually by provisioning new servers or automatically using cloud-based solutions like AWS Auto Scaling;
- Another option is vertical scaling, which involves upgrading the resources (CPU, RAM, etc.) of your existing server. This approach is suitable when you want to improve the performance of a single server;
- Containerization and orchestration tools like Kubernetes provide an efficient way to manage scalable applications. Kubernetes can automatically deploy and manage containers across a cluster of servers, making it easier to scale your applications up or down based on demand.
2. High Availability (HA):
- High availability (HA) is crucial for ensuring continuous service availability and minimizing downtime. HA configurations involve redundant systems that can take over if one server or component fails;
- One HA approach is to set up active-passive clusters, where one server (the active node) handles the traffic, while the other server (the passive node) is on standby. If the active node fails, the passive node takes over;
- Tools like Pacemaker and Corosync are commonly used to create HA clusters in Linux environments. These tools manage resources, monitor the health of servers, and automate failover processes;
- Cloud providers often offer built-in HA solutions. For example, AWS provides services like AWS Elastic Load Balancing (ELB) and Amazon Relational Database Service (RDS) with built-in HA features;
- Implementing HA requires careful planning and testing to ensure that failover processes work smoothly and data integrity is maintained.
By considering scalability and high availability in your server architecture, you can ensure that your infrastructure can handle increasing demands and maintain uninterrupted service, even in the face of hardware failures or other disruptions. These strategies are essential for businesses and organizations that rely on their servers for critical operations.
Conclusion
Opening a specific port on a server is a task that goes beyond the basics of firewall rules. It involves advanced techniques like port forwarding, dynamic port allocation, and load balancing. However, it also requires careful consideration of security aspects such as intrusion detection, two-factor authentication, and regular audits.
In today’s dynamic and interconnected digital landscape, the ability to manage server ports effectively is essential. Whether you’re a seasoned IT professional or a newcomer to server administration, the knowledge and skills you’ve gained from this comprehensive guide will empower you to optimize your server’s performance, enhance its security, and adapt to changing demands.
Remember that server port management is an ongoing process. Stay vigilant, keep up with security best practices, and adapt your configurations as your server’s needs evolve. By mastering the art of opening specific ports and maintaining them effectively, you’ll ensure that your server remains a reliable and secure cornerstone of your digital infrastructure.